BlackNote
An ephemeral secret sharing tool
Send an encrypted secret, retrieve it once, and it’s gone forever!
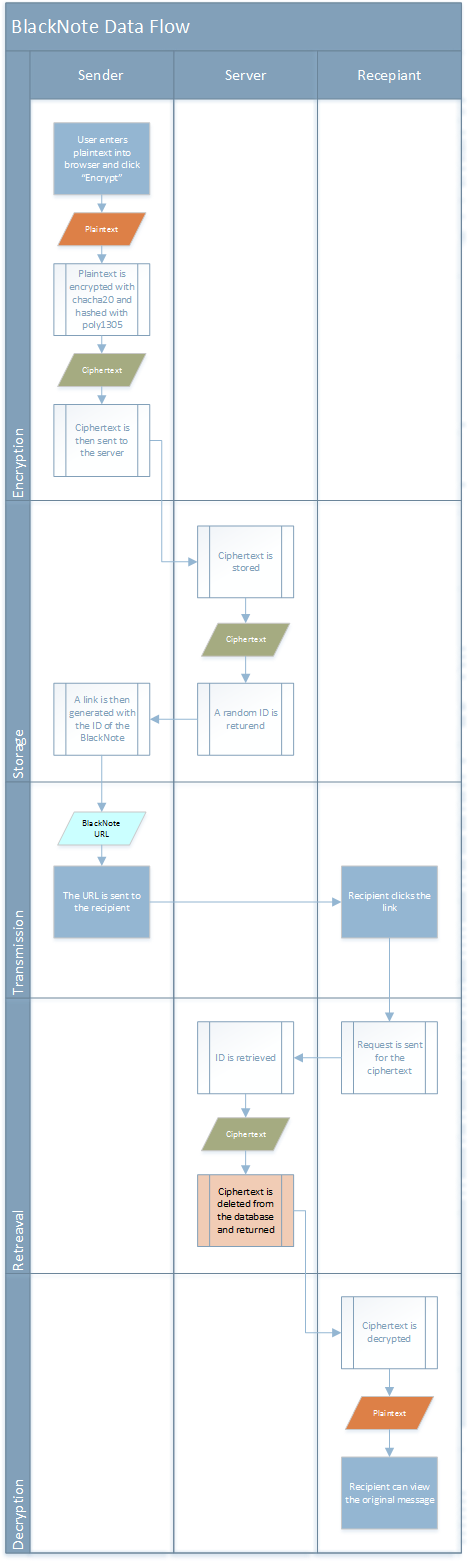
How it works
Technical Details
Libraries
We take the confidentiality of BlackNotes very seriously, and as such will only use software that is proven to work.
The only third party library BlackNote uses is the NaCL (pronounced "salt") cryptographic library. Which has been ported to JavaScript.
We only use one library to reduce the risk of vulnerabilities being introduced through extra (often unnecessary) third party libraries.
NaCL was chosen due to it's large usage world wide (libsodium), proven capabilities, and simplicity.
Nacl is the reference implementation for a complete and simple to use crypto library. It helps to remove all the intricate key manipulation operations traditionally used in crypto simplifies encryption to two calls, "box" and "unbox". It handles all the padding and timing and prevents many of the common mistakes developers make when using authenticated ciphers.
Encryption
BlackNotes are encrypted with 256 bit symmetric encryption (xSalsa20) using keys generated within the browser (Chrome, Firefox, IE).
The encryption keys are never passed to the server to ensure the integrity of all BlackNotes. This means that we could never recover any of the BlackNotes even if we wanted to.
Verification
Each BlackNote is cryptographically verified using the Poly1305 hashing algorithm.
If the integrity of the note is compromised, the decryption process will not be performed.
Technical Limitations
Cryptographic authentication is not performed.
This means that BlackNote cannot verify who sent a BlackNote or who reads a BlackNote.
When you receive a BlackNote link, your trust in the author's identity is only as strong as your trust in the transport mechanism through which you received the BlackNote link (email, chat, social media, IRC, etc.).
A higher trust in the transport mechanism means a higher trust in the authenticity of the BlackNote.
You can, however, be confident that the BlackNote you receive is exactly what the author intended (through cryptographic verification) and that no other party has accessed it.